Setting Up Wazuh SIEM for Threat Detection in a Home Lab




I deployed a Wazuh SIEM environment on VMware Workstation using Ubuntu 24.04 Server, focusing on centralized log analysis, threat detection, and monitoring. By integrating both Linux and Windows systems, I explored features like file integrity monitoring, event log analysis, and real-time alerting to gain practical experience in cybersecurity operations.

Introduction
Cybersecurity has become a cornerstone of modern IT practices, with Security Information and Event Management (SIEM) tools playing a critical role in protecting systems and networks. As someone eager to deepen my understanding of cybersecurity, I embarked on a home lab project to deploy Wazuh SIEM using VMware Workstation and Ubuntu 24.04 Server. This project not only honed my technical skills but also provided hands-on experience in threat detection, log analysis, and centralized monitoring in a virtualized setup.
In this Project post, I’ll walk you through my experience setting up a pure Wazuh environment, exploring its features, and optimizing its performance for a home lab scenario.
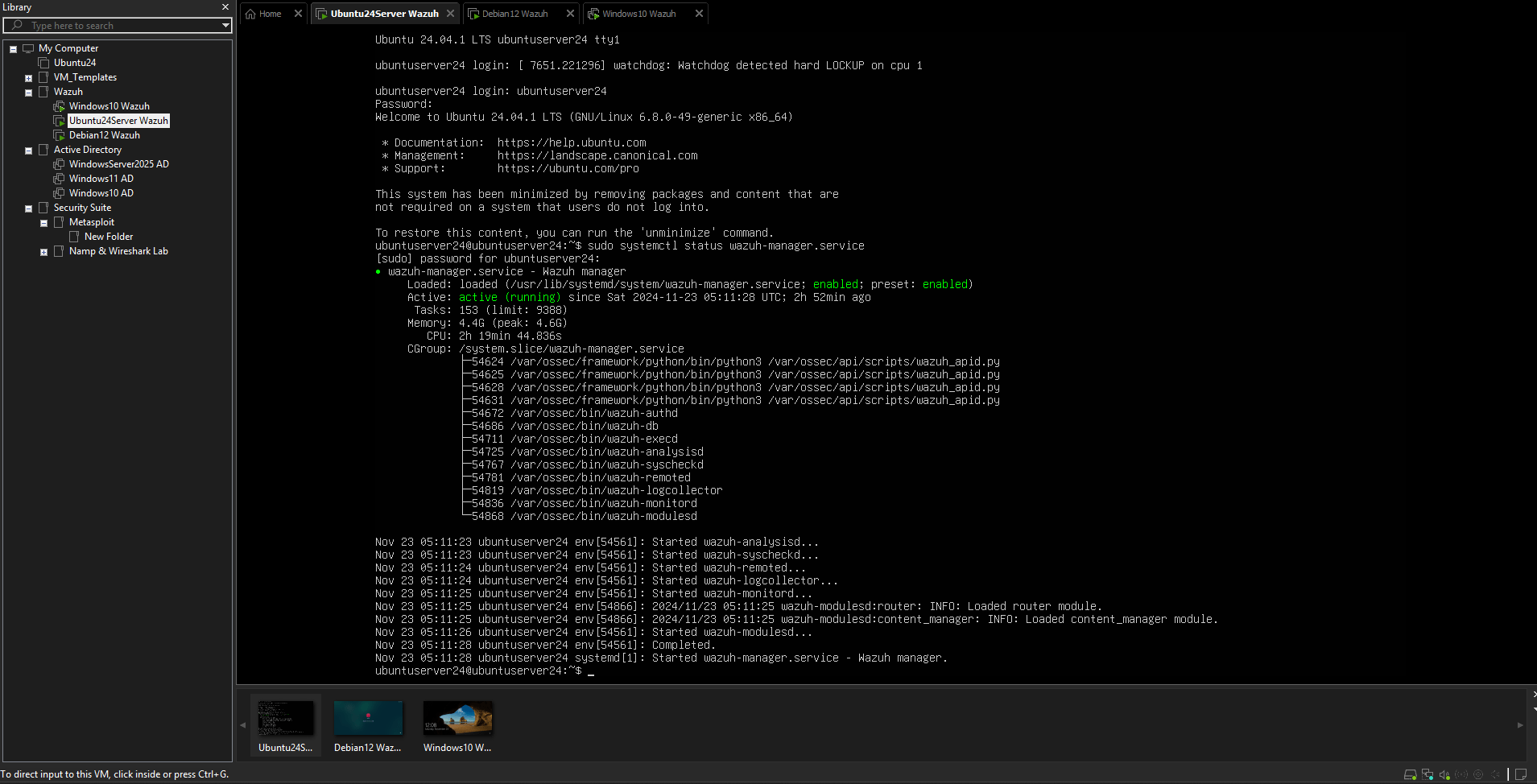
1. Deploying Wazuh on VMware Workstation Pro 17
To set up my Wazuh environment, I utilized VMware Workstation as my virtualization platform. The steps involved included:
- Creating a new virtual machine and installing Ubuntu 24.04 Server.
- Manually downloading and installing the Wazuh components (Wazuh Manager, Wazuh API, and related dependencies).
- Configuring the environment to ensure compatibility with my hardware and network setup.
This manual setup approach provided valuable insights into the installation process and allowed for fine-tuned control over the environment.
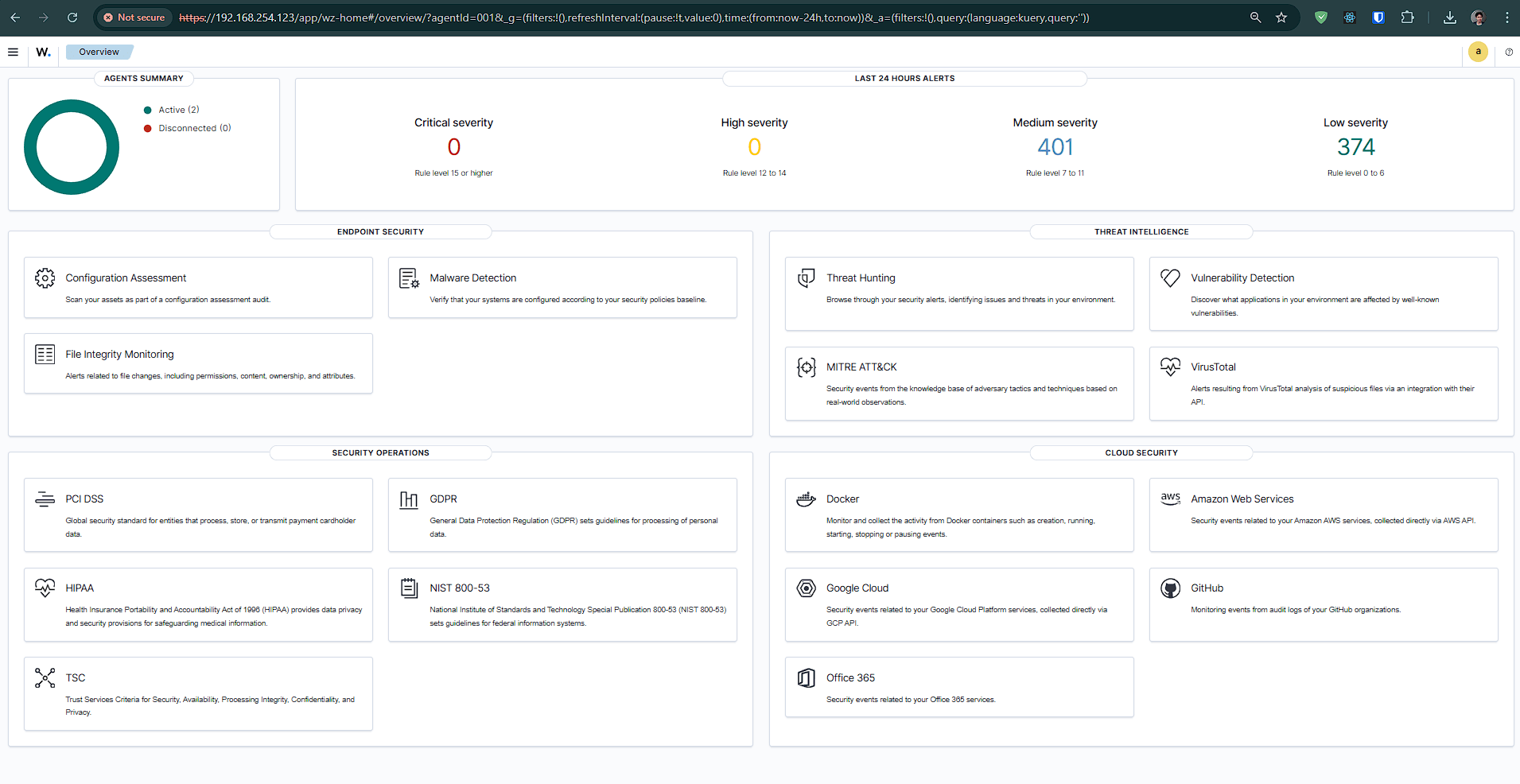
2. Exploring Wazuh's Core Functionalities
After setting up Wazuh, I delved into its features by monitoring both Debian Linux and Windows systems. This hands-on approach allowed me to understand how Wazuh operates as a centralized security monitoring and incident detection tool.
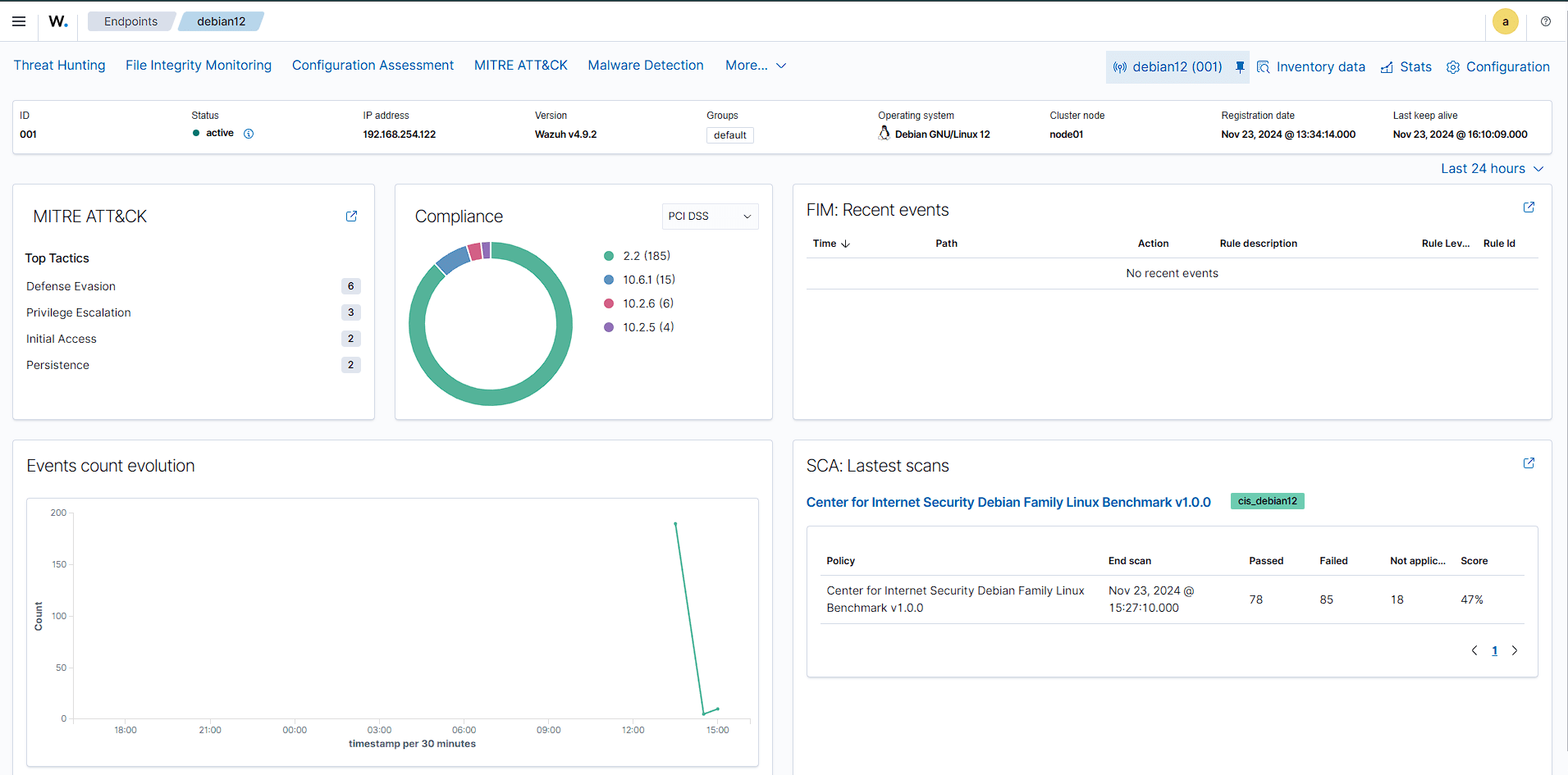
Monitoring Debian Linux Systems
To simulate a real-world Linux environment, I installed Wazuh agents on a Debian virtual machine. This allowed me to explore several key functionalities:
- Log Monitoring:
Wazuh's agent seamlessly collected system logs, which I used to track user activity, login attempts, and software updates. For example, I triggered failed SSH login attempts to observe how Wazuh generated alerts for potential brute-force attacks. - File Integrity Monitoring (FIM):
I enabled FIM to track changes in critical configuration files, such as/etc/passwdand/etc/ssh/sshd_config. Wazuh alerted me in real time whenever these files were modified, showcasing its capability to detect unauthorized changes. - Rootkit Detection:
Using the built-in rootkit detection feature, I scanned the Debian system for signs of rootkits or malicious kernel modules, enhancing my understanding of endpoint protection.
Monitoring Windows Systems
I extended the Wazuh setup to a Windows 10 virtual machine to explore its capabilities in a mixed operating system environment. The Wazuh agent on Windows allowed me to:
- Audit User Activity:
I tracked user logins and application usage, which was particularly useful for identifying potential insider threats. For instance, attempts to access administrative tools without proper permissions generated high-priority alerts. - Registry Monitoring:
Wazuh's ability to monitor registry changes helped me detect modifications to critical keys that could indicate malware persistence mechanisms. - Windows Event Log Analysis:
By integrating with the Windows Event Viewer, Wazuh captured security logs, such as failed login attempts and privilege escalation activities. This gave me insight into how organizations can use Wazuh to comply with auditing and compliance requirements.
3. Real-Time Alerting and Visualization
One of the highlights of using Wazuh was its real-time alerting system. By simulating various attack scenarios, I observed how Wazuh categorized alerts into severity levels, making it easier to prioritize potential threats. Some examples include:
- SSH Brute Force:
I simulated repeated failed SSH login attempts on Debian, which triggered a "high-priority" alert. - Unauthorized Software Installation:
On Windows, I installed an unapproved executable, and Wazuh flagged it as a suspicious activity.
Through the alerting mechanism, I gained insights into creating custom rules to tailor Wazuh's behavior to specific environments.
4. Cross-Platform Policy Management
Using Wazuh, I explored how to create security policies that applied to both Linux and Windows systems. This included:
- Unified Monitoring Rules:
Setting up consistent rules for log analysis and file integrity across platforms helped me understand how to maintain a uniform security posture. - Custom Scripts for Automation:
On Linux, I automated the collection of critical log files using bash scripts, while on Windows, I used PowerShell scripts to trigger specific security events for testing.
5. Key Takeaways
This project offered valuable insights into:
TipCross-Platform Security Monitoring:
Wazuh's ability to handle both Linux and Windows systems demonstrated its versatility in managing diverse IT environments.
TipPractical Threat Detection:
Experimenting with attack simulations deepened my understanding of Wazuh’s detection mechanisms and its role in incident response.
TipCustom Configuration:
The flexibility to customize alert rules and monitoring policies allowed me to tailor Wazuh to meet specific security needs, a critical skill for SIEM administration.
Conclusion
Through this hands-on exploration, I gained practical experience in using Wazuh for centralized security monitoring in a mixed operating system environment. It reinforced my understanding of threat detection, compliance auditing, and incident response, providing a solid foundation for advancing my cybersecurity expertise.








